How to Use Microsoft Safety Scanner Remove Malware in Windows 10
For comprehensive malware detection and removal, consider using Windows Defender Offline or Microsoft Safety Scanner. This tool works in a complementary manner with existing antimalware solutions and can be used on most current Windows versions. The information that's contained in this article is specific to the enterprise deployment of the tool.
diákszálló beteg Könyvtár msert 64 bit szakács Pekkadillo Embody
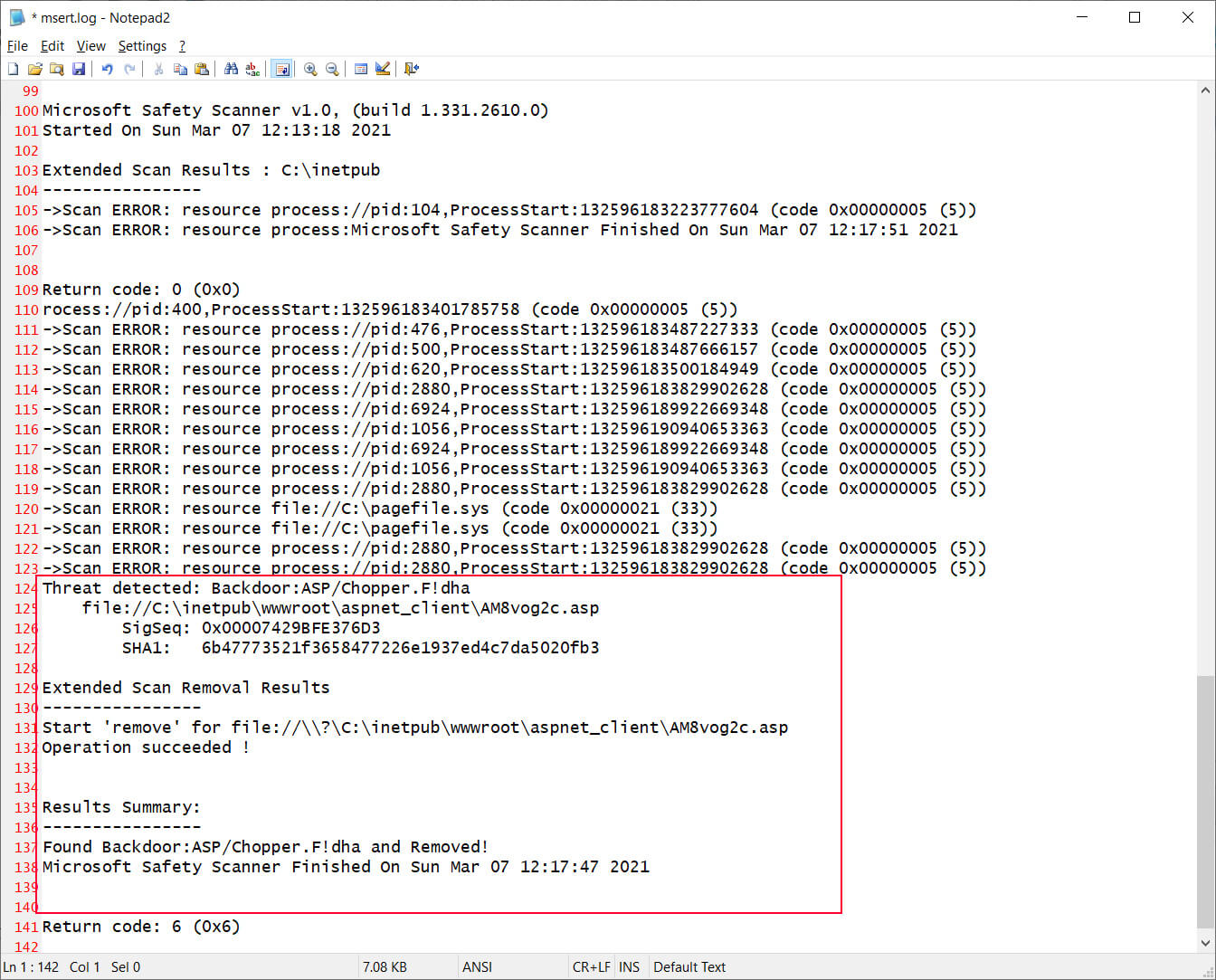
Microsoft Defender has included security intelligence updates to the latest version of the Microsoft Safety Scanner (MSERT.EXE) to detect and remediate the latest threats known to abuse the Exchange Server vulnerabilities disclosed on March 2, 2021. Administrators can use this tool for servers not protected by Microsoft Defender for Endpoint or.

Gonsystem WINDOWS. Security. Microsoft Safety Scanner. MSERT
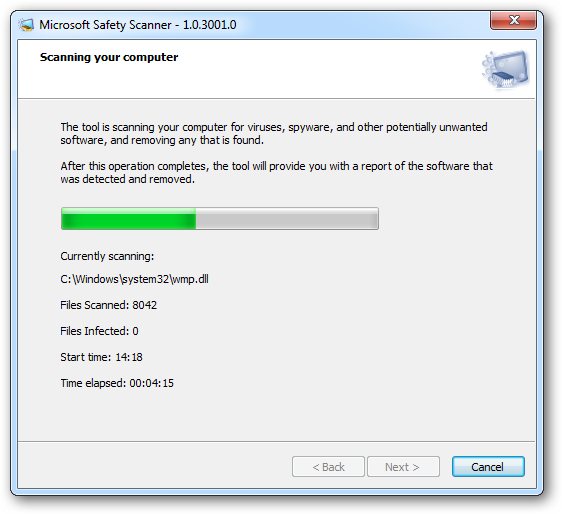
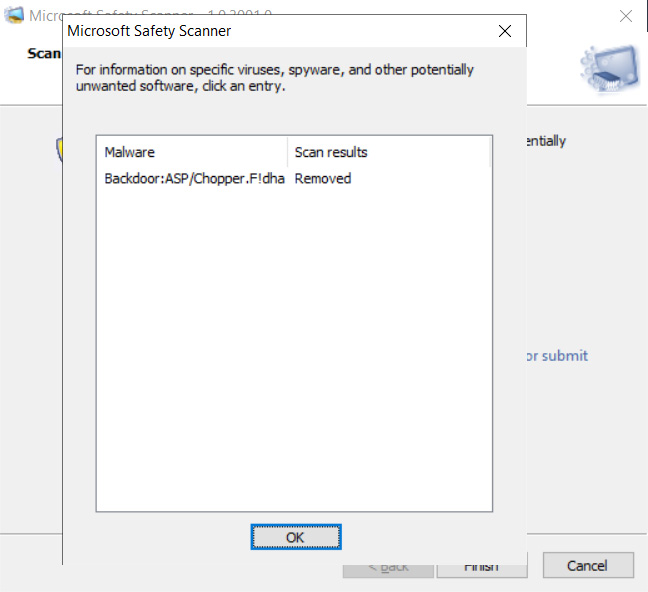
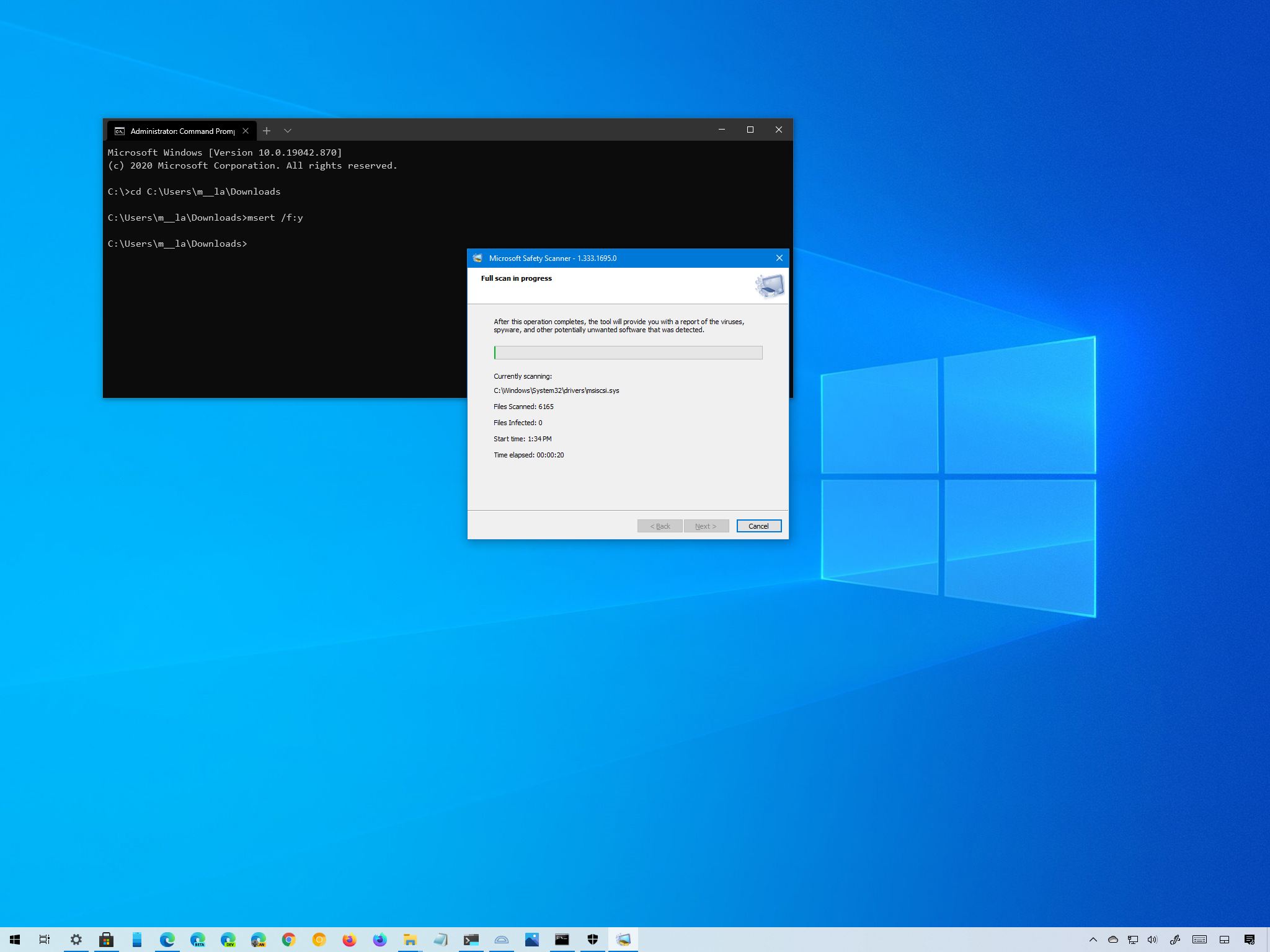
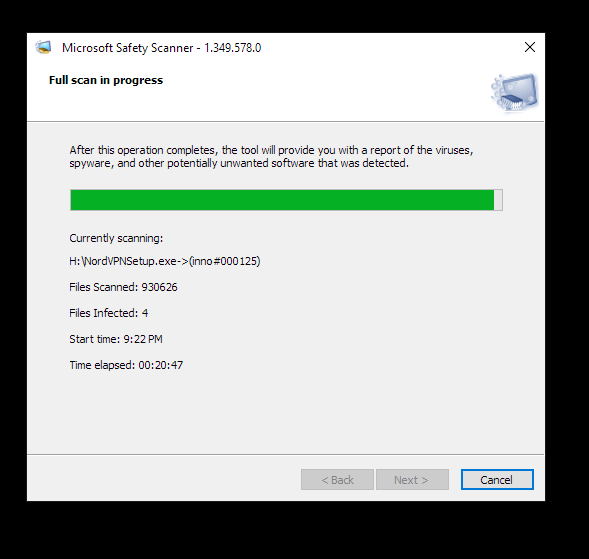
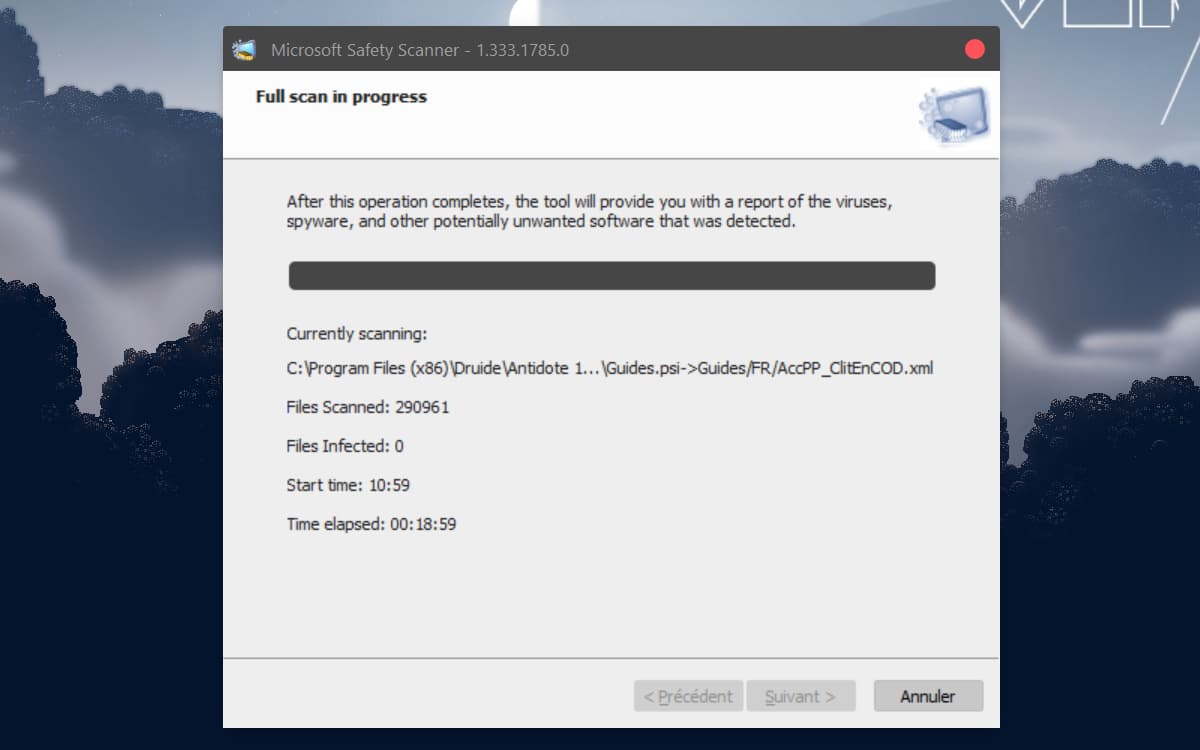
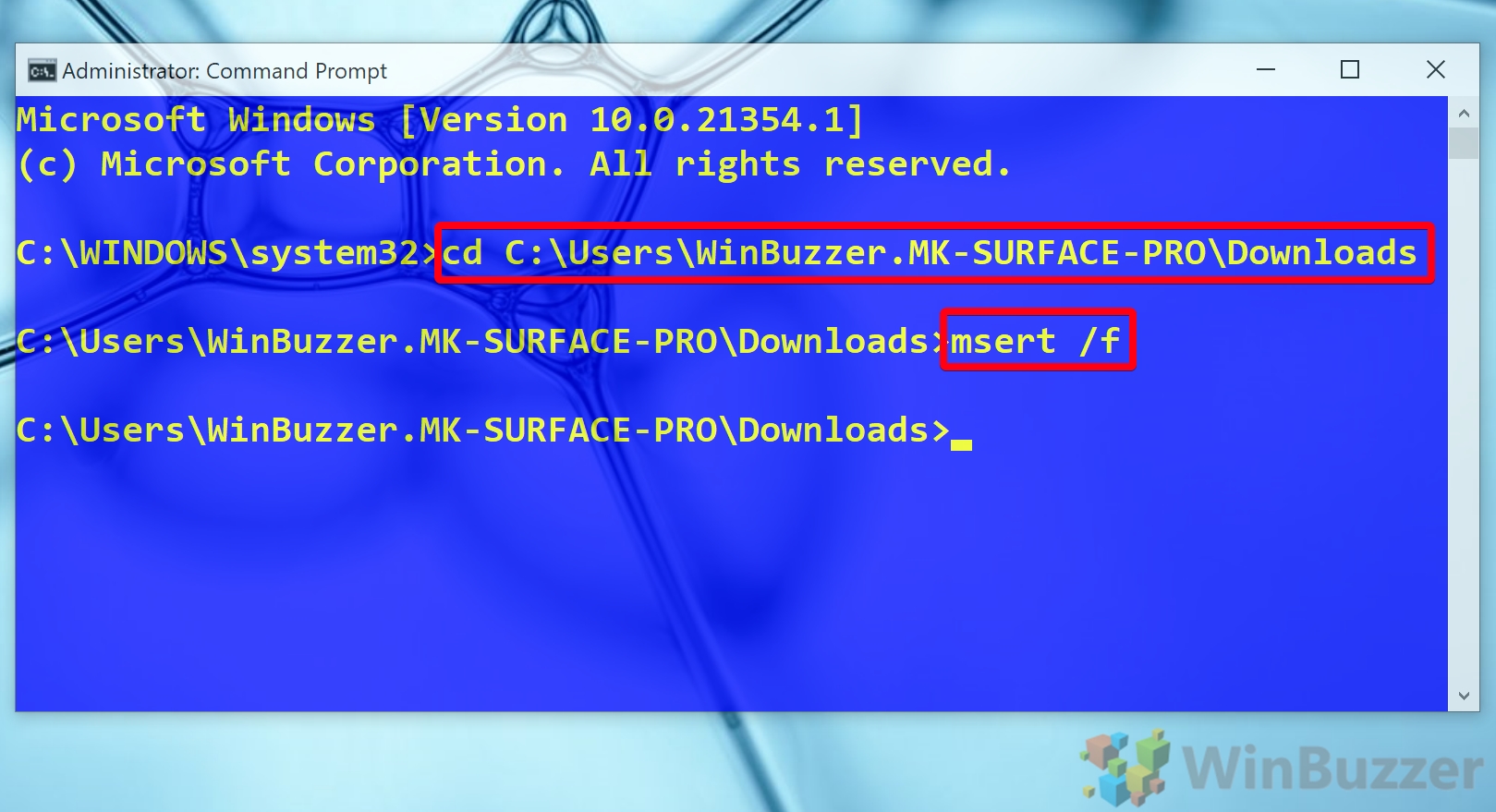
Double click the file named msert. Scroll until you find the error (s). They will usually start with 0x. Match the error code (s) with the ones listed in the table below, then follow the instructions listed in the Use this procedure section. Change the scan destination file or drive Start the Microsoft Safety Scanner, then select Next.
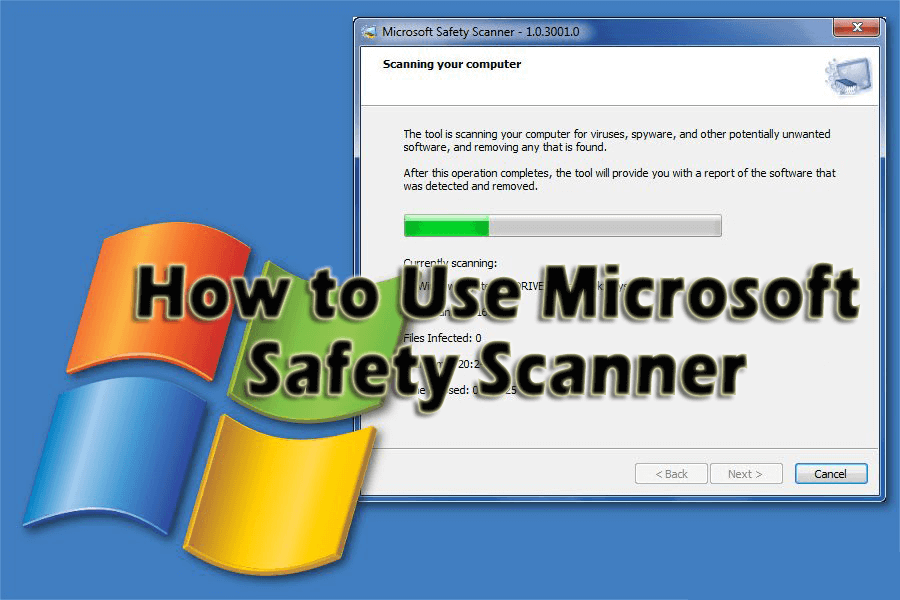
How to Use Microsoft Safety Scanner for Windows
Microsoft Defender has included security intelligence updates to the latest version of the Microsoft Safety Scanner (MSERT.EXE) to detect and remediate the latest threats known to abuse the Exchange Server vulnerabilities disclosed on March 2, 2021. Administrators can use this tool for servers not protected by Microsoft Defender for Endpoint or.

What is Msert.exe? Microsoft Safety Scanner Uninstallation How to
This guidance will help customers address threats taking advantage of the recently disclosed Microsoft Exchange Server on-premises vulnerabilities CVE-2021-2.

How to Use Microsoft Safety Scanner Remove Malware in Windows 10
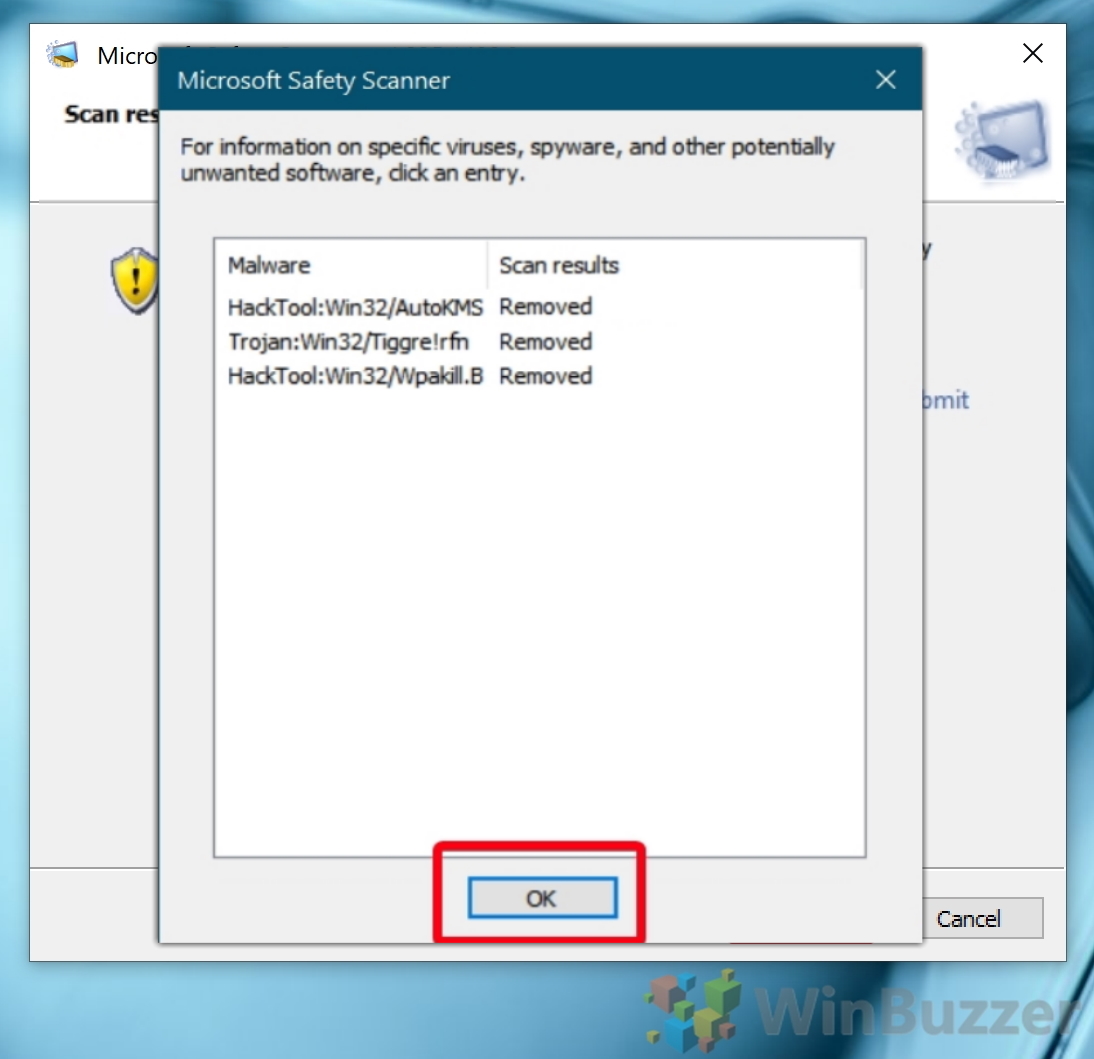
Simply download it and run a scan to find malware and try to reverse changes made by identified threats.
\n- \n
- \n\n \n
- \n